Multi-factor Authentication Threats Heat Up
Just a few months ago, we wrote an article about the dangers of using SMS (text) to support multi-factor authentication (MFA), called Breaking the...
1 min read
Stephanie Goetz : Mar 17, 2023


Since the pandemic and the rise of work at home, we have become very familiar with Multi-Factor Authentication (MFA). Typically, this is implemented as a One-Time Password (OTP) delivered via an application on a smartphone, phone call, or SMS text.
Like any high-value information, this has become vulnerable to social engineering. Scammers trick people into giving the codes via phishing emails, phone calls, fake portals, and other creative means.
CISA released guidance on how to phish-proof these implementations in a recent publication I’ve found very helpful: https://www.cisa.gov/sites/default/files/publications/fact-sheet-implementing-phishing-resistant-mfa-508c.pdf and https://www.cisa.gov/sites/default/files/publications/fact-sheet-implement-number-matching-in-mfa-applications-508c.pdf.
Here are some key takeaways from this guidance.
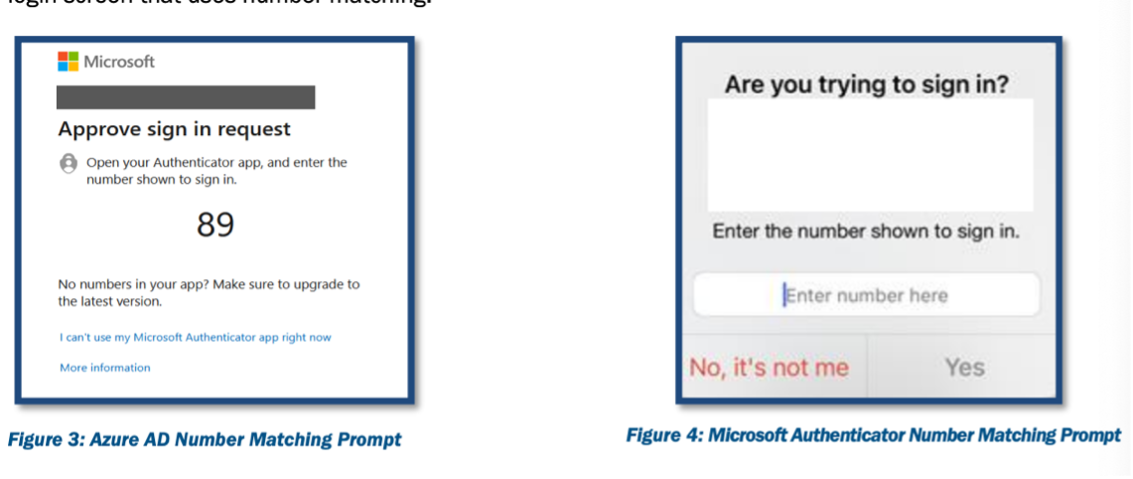
Many common vendors support this including Microsoft, Duo, and Okta.
I am excited about the number matching options as it seems the most feasible without an Identity Management program overhaul. The stronger methods may be best for high-value accounts, such as administrator accounts and domain controllers.
If you have any questions or need help, please contact us at support@bedelsecurity.com.

Just a few months ago, we wrote an article about the dangers of using SMS (text) to support multi-factor authentication (MFA), called Breaking the...

It’s been a long and crazy two years since Covid showed up and changed the world. Yes, a lot of things are different now, but I’d like to take a few...

Over the past month, many have written about the latest LastPass breach. If you have not kept up with the breach, you can see the disclosure from...